Blog

7 Reasons to Upgrade Your Legacy SCADA System to the Ignition Platform
Do you have a legacy SCADA system in your manufacturing facility that is creaking at the seams? Are you worried about the risks posed by your outdated SCADA system, or are you frustrated by the limitations it places on your modernisation efforts? Are you simply fed up with the high and difficult-to-control costs? Upgrading your legacy SCADA system to the Ignition platform is the solution.
SL Controls is a certified Ignition integrator, and we have extensive experience migrating manufacturing operations, especially those in the life sciences sector. From our experience, here are the seven main reasons for starting the process of upgrading your legacy SCADA system to the powerful, modern, and highly flexible Ignition platform.
You Can Reduce and Simplify License Fees
The licensing fees for many SCADA platforms are high and extremely complex to manage and control. It is easy for fees to become exorbitant to the point where the potential increase in fees can put the brake on production line modernisation, upgrade, and improvement projects.
In many situations, it is possible to reduce your licensing costs with Ignition. This is because Ignition is based on an unlimited license model. The unlimited license model means you don’t incur additional costs when you add another client or production line. When you buy an Ignition server license, everything is covered, regardless of how many clients or tags you add. This not only reduces your costs but also makes it significantly more straightforward to manage.
Your Operations Will Be More Secure
Many legacy SCADA systems have minimal or outdated security technologies. This can expose your production lines and wider business operations to substantial cybersecurity risks, especially as you work to increase connectivity, automation, and your use of data.
Ignition is built with security as a core priority, so it features the latest technologies. It is also continuously updated, enhancing security and covering-off new and emerging threats.
Your Legacy SCADA is No Longer Supported
Your current SCADA system could have reached its end-of-life (EOL) and is no longer supported, or the available support might be patchy or non-existent for another reason. You can even have internal support issues, with expert operators nearing retirement age.
EOL and unsupported SCADA systems expose your manufacturing operations to additional risks. They also limit your ability to modernise.
Ignition is a growing platform that is continuously being improved. It has a strong support offering, experienced and committed integrators (including us at SL Controls), and an active community. Whatever support you need, it is available on the Ignition platform.
You Can Do More Than SCADA With Ignition
Ignition is a highly flexible platform with a robust development environment that allows our team of experts to create any type of industrial application.
This includes, for example, eliminating the need to have a SCADA system and a separate MES. Ignition can do it all in one platform. Ignition can also be used as a paper-to-glass solution where you can digitalise existing manual or paper-based processes and incorporate them into the SCADA system as part of the upgrade.
Download our whitepaper on flattening your manufacturing software stack to find out more.
You Can’t Integrate New Technology with Your Legacy SCADA System
It is often difficult or even impossible to fully integrate new technologies with legacy SCADA systems. There can also be compatibility issues when you need to install new production equipment. These integration and compatibility problems can again limit your ability to modernise, impacting performance and giving your competitors an edge.
The Ignition platform eliminates integration and compatibility issues.
Ignition is Highly Adaptable
One of the reasons that companies delay the introduction of new technologies like Ignition is the skills of operators. Existing staff might be very familiar with your legacy SCADA system. They might also be comfortable with it too, so are resistant to change.
Ignition is highly adaptable, however, so the transition to the new platform can be made as seamless as possible. Our team at SL Controls can even match the look and feel of Ignition screens to your legacy SCADA system, increasing familiarity for operators.
Improve Performance, Compliance, Oversight, and Control
Ignition will unleash the power of data in your manufacturing operations while making it easy to control, monitor, and analyse processes. You can also continuously optimise key performance metrics, including OEE, as well as improving compliance processes with automated auditing of every action and interaction.
Migrating to Ignition
The benefits we have highlighted above mean you can expect a rapid return on investment when you upgrade your existing SCADA system to the Ignition platform. In closing, it is also important to highlight that migrating to Ignition is not a one-size-fits-all process.
At SL Controls, we will customise your Ignition platform migration according to your requirements, capabilities, existing technologies, budget, skills, and desired outcomes. Get in touch with us today to find out more.

How Digital Transformation Drives Significant CAPA Quality Process Efficiency Savings
In regulated industries, CAPA (Corrective and Preventative Action) is a core component of your Quality Management System (QMS). Your CAPA quality process is essential for regulatory compliance reasons, but CAPA is also about improving product safety, operational safety in your plant, productivity, OEE, cost-base, and more – the list goes on.
CAPA aims to identify and stop problems and non-conformities from reoccurring (or occurring in the first place) to ensure continuous quality improvement.
While CAPA is important, the reality in many regulated manufacturing organisations is that it is also time-consuming, inefficient, and unnecessarily costly. Results from CAPA quality processes are often sub-optimal, and even with the best efforts and intentions, your organisation can remain exposed to compliance, commercial, and reputational risks.
Furthermore, most of the time and resources expended on CAPA are focused on the “C” element – corrective actions. This can be because of resource availability as well as a lack of complete or accurate data to work through the preventative component.
In the real world, CAPA is more like EBCAAOPAWDIAAWHETTCAPA – “event-based corrective actions and occasionally preventative actions when data is available and we have enough time to conduct a proper analysis”.
That’s a bit of a mouthful so we’ll stick to CAPA but in doing so, we’ll answer two fundamental questions:
- Why are CAPA quality processes inefficient?
- How can CAPA quality processes be improved?
Why Are CAPA Quality Processes Inefficient?
All manufacturing facilities are unique, with different challenges, processes, and systems. As a result, there is no single answer to the question of CAPA quality process inefficiency. That said, one of the major contributory factors is paper-based processes.
Paper-based processes are in themselves inefficient, and they are prone to human error. Paper-based processes also make it more difficult to quickly identify the problems and non-conformities that CAPA quality processes aim to correct. Predicting potential problems and non-conformities before they occur so preventative actions can be taken is even more difficult.
Even when problems or non-conformities are identified, paper-based processes make the next crucial stage of CAPA costly and time-consuming – investigating the non-conformity to understand the impact, level of risk, and root cause. Accurate and complete paper records may not exist and even when they do, it is often challenging to efficiently locate and analyse them.
So, paper-based systems in regulated manufacturing facilities are a major cause of inefficiency in CAPA quality processes.
How Can CAPA Quality Processes Be Improved?
Digital transformation is the solution, where paper-based systems and processes are digitalised. That doesn’t just mean digitising the storing of records, but digitalising complete processes so the collection, communication, and analysis of records are all automated and digitalised.
Digitalising CAPA quality processes is part of this solution, but the bigger and more impactful element is to progress digital transformation initiatives in your facility. An example is to implement a modern MES/SCADA solution that could digitalise at least 50 percent of current paper-based processes within six months and deliver rapid returns on investment.
Read our whitepaper on how modern solutions make it possible to implement a single system combining both MES and SCADA functionality, reducing costs, installation complexity, and ongoing usability.
By implementing a paper-to-glass solution, problems and non-conformities can be identified and investigated quicker, leading to the faster implementation of corrective actions.
You can also then move more into prediction-based CAPA, where potential problems are identified and corrected before they occur.
Digital Transformation Beyond Quality Control
Of course, the benefits of modern MES-SCADA solutions and digital transformation initiatives go beyond making CAPA quality processes more efficient. Given the crucial role that CAPA has in terms of your QMS and overall operational performance, the impact of digital transformation on quality control and continuous improvement should not be underestimated. In many situations, it justifies the investment even before you consider increased automation, greater availability of real-time data, and improved productivity.
So, the summary is digital transformation will drive significant efficiency savings in your CAPA quality processes.
Download the Whitepaper
Full Stack OT Platforms

Why platforms like Ignition MES and Ignition SCADA are needed and selection best practices
Infographic: Combined SCADA and MES Platforms Explained
Download the infographic as a PDF
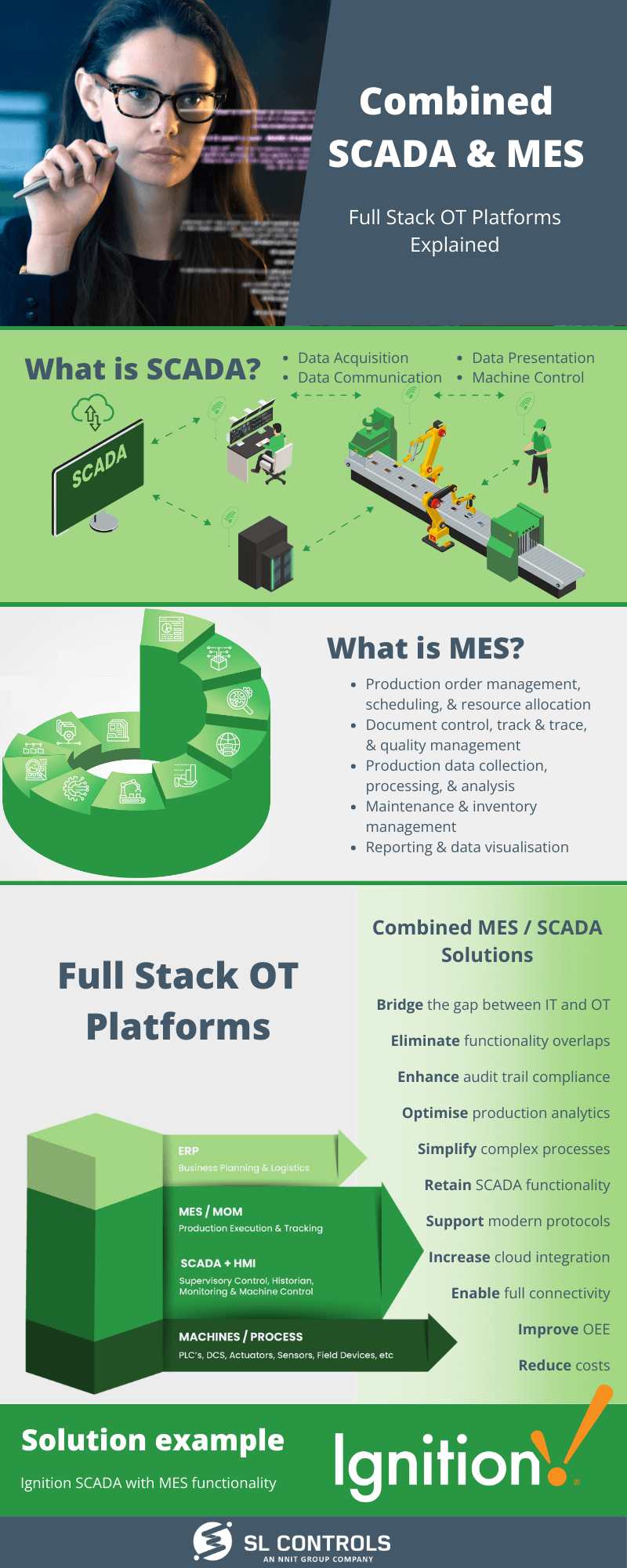
Combined SCADA and MES – Full Stack OT Platforms Explained
Full Stack OT (operational technology) Platforms combine SCADA and MES (manufacturing execution system) functionality into one solution. Here’s an overview:
What is SCADA?
- Data acquisition
- Data communication
- Data presentation
- Machine control
What is MES?
- Production order management, scheduling, and resource allocation
- Document control, track & trace, and quality management
- Production data collection, processing, and analysis
- Maintenance and inventory management
- Reporting and data visualisation
Full Stack OT Plaforms – Combine MES / SCADA Solutions
- Bridge the gap between IT and OT
- Eliminate functionality overlaps
- Enhance audit trail compliance
- Optimise production analytics
- Simplify complex processes
- Retain SCADA functionality
- Support modern protocols
- Increase cloud integration
- Enable full connectivity
- Improve OEE
- Reduce costs
Solution Example
Ignition SCADA with MES functionality – to learn more, download our free whitepaper: Full Stack OT Platforms – Why they are needed and selection criteria best practices
SL Controls in now NNIT. Read more about NNIT’s vendor evaluation strategy.

Combined SCADA and MES Solutions for Pharmaceutical and Medical Device Manufacturers
The traditional manufacturing software stack – often referred to as the ISA-95 model – is well established in a range of industries and sectors, including the pharmaceutical and medical device manufacturing industries. Companies have built structures and processes around this model that facilitate profitable production, regulatory compliance, and effective quality control.
However, hierarchical structures like the ISA-95 manufacturing stack are becoming less and less common in the modern and increasingly digitalised world. What does this mean for manufacturers in the life sciences sector?
Flattening the Stack
In the latest whitepaper published on our website, my colleague and SL Controls Chief Technology Officer Paul Clarke puts forward compelling arguments to move away from the traditional hierarchical structure to a flatter software stack. You can read the whitepaper here.
Paul’s conclusions are based on the operational requirements of manufacturers in the life sciences sector today and in the future, as well as the modern Full Stack OT (operational technology) Platforms that are now available.
A good example of a Full Stack OT Platform is Ignition by Inductive Automation. The Ignition platform offers both SCADA and MES functionality and, crucially, there is no compromise. In other words, you don’t need to compromise on SCADA functionality to achieve MES capabilities and vice versa.
The Benefits of Combined SCADA and MES Solutions
At SL Controls, we have a lot of experience implementing Full Stack OT Platforms like Ignition in life sciences sector operations, and we have experience of the benefits this type of solution brings. Those benefits include:
- Solving connectivity issues between systems and equipment at the plant and enterprise level with those on the factory floor.
- Achieving support for increasingly common protocols, including MQTT (Message Queuing Telemetry Transport).
- Streamlined and more efficient regulatory compliance, especially in relation to audit trails and document control.
- Simplified and flexible cloud integration and the associated benefits that cloud integrations bring.
- Enhanced manufacturing analytics with digestible and actionable dashboards.
- Reduced process complexity.
- Improved OEE (overall equipment effectiveness).
- Reduced costs, including operational, training, licensing, and hardware costs.
The Next Steps
Whether you are looking for a new SCADA solution or want to enhance your operations by improving the integration between IT systems and OT systems (known as bridging the IT/OT gap), it is beneficial to consider a combined platform – a Full Stack OT Platform.
In the whitepaper mentioned earlier, Paul says the first step in the process is to define what is required. This includes clarifying what you want to achieve with the project today and in the future. Getting a full understanding of your current infrastructure is also important, both the systems and hardware that make up your IT infrastructure and the equipment and systems that come under the OT heading.
As part of the above process, it is essential to identify the legacy systems that need to be retained and integrated into the new platform.
The above is all in addition to assessing the resources and budget you have available, as well as the consultancy, planning, engineering, validation, and compliance support you will need from an experienced and certified integrator like SL Controls.
To find out more and to discuss the advantages that Full Stack OT Platforms can bring to your pharmaceutical or medical device manufacturing operations, get in touch with us at SL Controls. Or you can email me directly on [email protected].

How to Choose the Right Full Stack OT Platform
Manufacturers in the life sciences sector have been going through a period of continual change as organisations automate processes, integrate equipment, and make better use of data along Industry 4.0 principles. Part of this process of change is the growing trend to switch to Full Stack OT Platforms.
Full Stack OT (operational technology) Platforms are single-platform solutions that offer the functionality and features of both SCADA and MES systems. By implementing a Full Stack OT Platform, you will simplify your software stack while improving oversight, control, and productivity. Levels of integration will improve vertically through the organisation, from factory floor to ERP systems, and horizontally across your supply chain.
Modernising the Traditional ISA-95 Software Stack
The ISA-95 manufacturing software stack can trace its origins back to the 1990s. It has evolved over time, with the current versions typically having five levels:
- Level 0 – Component Level
- Level 1 – Field Level
- Level 2 – Operation and Control Level (or the Supervisory Control Level)
- Level 3 – Plant Level
- Level 4 – Enterprise Level
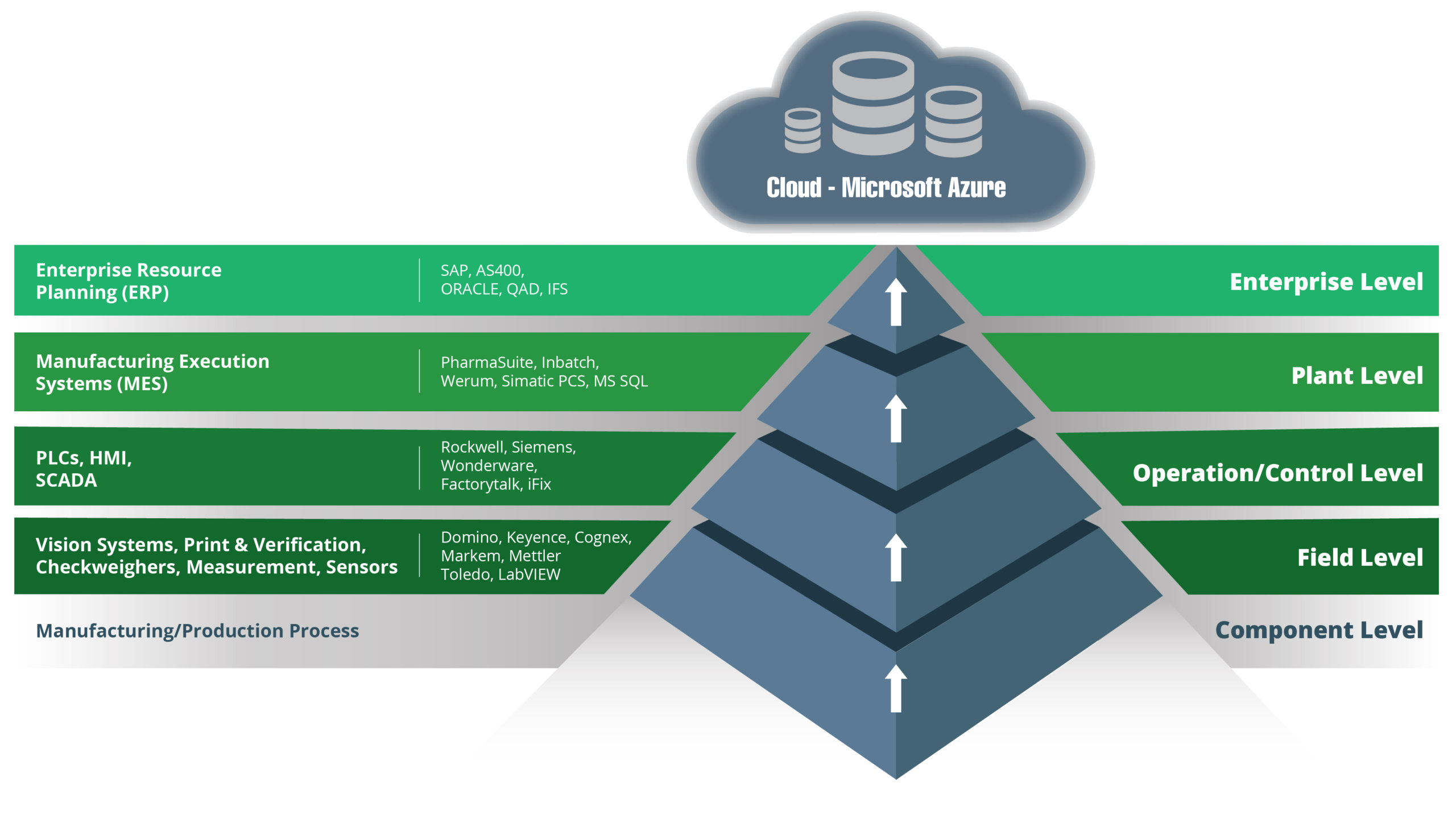
Advances in technologies mean there is now considerable functionality crossover between the best SCADA and MES systems. Modern platforms also offer additional benefits, including enhanced integration and better use of data.
Paul Clarke, CTO at SL Controls, said:
“Modern platforms also make it possible to unleash the true power of data in your organisation through data historian technologies, advanced analytics, and reporting capabilities, and by enabling automated decision-making.”
The Full Stack OT Platforms that Paul is referring to make it possible to flatten the traditional ISA-95 stack and move away from its hierarchical structure. In its place comes more of an eco-system solution that is better able to bridge the gap between IT and OT.
Choosing the Right Full Stack OT Platform
SL Controls has real-world experience of implementing Full Stack OT Platforms in life sciences sector manufacturing organisations. We have used that experience to develop and refine a selection process that ensures you get a solution that fully meets your requirements and delivers tangible results.
We have produced a whitepaper, authored by our CTO Paul Clarke, that makes the case for flattening the ISA-95 stack and switching from separated systems to Full Stack OT Platforms. Paul outlines the benefits of this approach for manufacturers in the pharmaceutical and medical device industries, before explaining the steps required to ensure the right platform is selected.
With our experience and expertise, we can assist with your technology and change management project, from planning and consulting to implementation and operation.
Download our whitepaper “Full Stack OT Platforms – Why They Are Needed and Selection Criteria Best Practices”.

Understanding Cybersecurity Risks When Bridging the IT/OT Gap
Bridging the gap between IT and OT is a key objective for a growing number of organisations in the life sciences sector. The benefits of doing so are substantial, including having increased OT oversight and being able to use OT data to transform business operations. When bridging the IT/OT gap, it is essential to understand the cybersecurity risks that are involved and how to mitigate them.
Cyberattacks on any organisation can have significant financial and reputational ramifications. In the life sciences sector, there are additional risk factors that are arguably even more important, including the risk to patient safety.
Therefore, prioritising and investing in cybersecurity is essential for life sciences sector organisations.
Competing Priorities
By taking steps to bridge the IT/OT gap, cybersecurity risks increase. In simple terms, IT security is mature and well-established. It isn’t perfect, but IT security is substantially more advanced than OT security.
Potential cybersecurity outcomes include production line shutdowns or compromised product batches. Bridging the IT/OT gap can also expose IT systems to OT cybersecurity vulnerabilities.
OT Cybersecurity Vulnerabilities
There are many reasons why bridging the IT/OT gap can increase cybersecurity risks, but most come under the heading of existing OT vulnerabilities, starting with the vulnerabilities created by legacy systems.
Legacy Systems
Legacy systems are common in many life sciences manufacturing facilities, and they are often central to operations. They also often run on outdated and potentially vulnerable software. Historically this has been tolerated, as uptime was considered more important than fixing something (by updating the software) that isn’t, from an operational perspective, broken.
Connecting these legacy systems changes the equation.
Cybersecurity becomes an essential consideration when connecting equipment to the internet that has never been connected before and, in some cases, was never intended to be connected when it was first developed and manufactured. These legacy OT systems typically don’t have built-in security features and where they do exist, they are often minimal and outdated.
Organisational Culture
The biggest cybersecurity challenges that organisations face are typically not related to equipment or machines. The biggest challenges relate to people, as people are often the softest entry point for a cyber-attack.
This applies when bridging the gap between IT and OT. You have the same people-related security issues that apply to any connected system, but you also have the added complication of disconnected teams. This common lack of coordination and collaboration between IT and OT teams increases cybersecurity risks.
Multiple Systems
OT typically comprises a mix of old and new technologies, equipment, and platforms all with different security features and vulnerabilities. The simple fact of having multiple systems increases cybersecurity risks.
There are then additional risk factors, such as OEMs being connected to their equipment for performance monitoring and maintenance reasons. While these types of connections bring benefits, they also create additional entry points for cyber-attacks.
All Production Lines Are Prototypes
No two production lines are the same, even if they are manufacturing the same product. As a result, all production lines in the life sciences sector are essentially prototypes with bespoke integrations and connections. This reality adds to the cybersecurity challenge.
Growth of the IIOT in Health Care
The industrial Internet of Things (IIOT) is transforming many aspects of healthcare with devices that monitor patients and control the administration of treatments automatically and in real-time.
All that new patient data increases the potential value of life sciences sector companies in the eyes of hackers and cybercriminals.
Existing Cybersecurity Solutions
It’s also important to consider existing cybersecurity solutions, as most are aimed at IT rather than OT environments. They are feature-packed, highly robust, and powerful, but they have an IT rather than OT focus.
This can present challenges in OT environments that exacerbate the cybersecurity problem.
Take multi-factor authentication (MFA) as an example. MFA is used in many organisations to beef up cybersecurity and ensure accounts, platforms, and systems are less vulnerable to weak, shared, or hacked passwords.
In a typical office environment, MFA is a small hurdle for users to overcome. They simply use their phone to get the access code from a text message or app to authenticate their login. How can you replicate this in the hygiene-controlled environments of pharmaceutical manufacturing facilities, medical device cleanrooms, or pharma laboratories?
An Introduction to Mitigating Cybersecurity Risks When Bridging the IT/OT Gap
We will explore in more detail in a future blog the mitigation steps that can be taken to reduce cybersecurity risks when bridging the IT/OT gap. The main points include:
- Flatten the stack – reduce the number of systems, particularly in the OT stack, to reduce the potential attack surface for cyber criminals.
- Technical steps – examples of technical steps that can be taken to enhance cybersecurity when bridging the IT/OT gap include creating secure access protocols at every endpoint, encrypting network traffic, and protecting both IT and OT with firewalls.
- Organisational management and people – ensure IT and OT teams work together, particularly on cybersecurity issues, while taking a holistic approach to security that includes both IT and OT teams. Continuously training staff on cybersecurity issues is also important.
- Vendor management – OEMs and software vendors are critical cybersecurity components, so they should be thoroughly vetted and managed.
The most important factor to mitigate risks when bridging the IT/OT gap is to put cybersecurity at the centre of your planning, with cybersecurity considerations factored into every decision and strategy implementation step.

Externalisation in the Life Sciences Sector Through the Growth of CDMOs and CMOs
CDMOs (contract development and manufacturing organisations) and CMOs (contract manufacturing organisations) have been a feature of the life sciences sector for many decades. However, this part of the sector is changing and growing, making externalisation an even more critical element of worldwide pharmaceutical and medical device development and production.
A lot of the change taking place within CDMOs and CMOs concerns the business models and strategies they are increasingly deploying. Traditionally, CDMOs and CMOs focused on capacity, often acquiring manufacturing facilities as the primary method of business growth. Today, however, the focus of CDMOs and CMOs is on offering value-adding services.
Capacity is still important, but the ability to offer hard-to-find expertise, industry-leading knowledge, and advanced technologies are some of the things that are making partnerships with CDMOs and CMOs such an attractive option for pharmaceutical and medical device companies.
An example is the ability to manufacture complex and challenging cell and gene therapies. CDMOs and CMOs with this capability offer so much more than straightforward manufacturing capacity.
How CDMOs and CMOs Work
The partnership arrangements between life sciences sector companies and CDMOs/CMOs vary depending on requirements and objectives. For example, large pharmaceutical and medical device companies often choose to outsource elements of a product development project to a CDMO. They could do this because of internal capacity or capability challenges, i.e., where internal resources are either not available or don’t have the right expertise or skillsets.
Startup companies, on the other hand, commonly choose to outsource entire projects, from product design and development to regulatory support to manufacturing and commercialisation. Choosing this approach means the startup doesn’t have to invest in premises, equipment, people, and technologies.
Common services that CDMOs and CMOs offer include drug development, medical device design, regulatory support, and manufacturing.
The Advantages of Partnering with a CDMO or CMO
Reduced Risk
In general, outsourcing to a CDMO or CMO can distribute the risks associated with manufacturing, especially in startups where a company doesn’t have prior manufacturing experience.
However, there is an even more important factor specifically related to the life sciences sector – mitigating business and process risks without compromising patient safety, compliance, or manufacturing productivity. One example is the risk of supply chain security, as partnering with a CDMO or CMO can improve the robustness of a product’s supply chain.
Speed to Market
Using a CDMO or CMO can accelerate the process of getting a product to market, especially if the partner has available capacity. Given the high levels of competition in the life sciences sector, faster speed to market timescales can have a considerable impact on everything from competitiveness to viability to profitability.
Access to One-Stop-Shop Providers
CDMOs often promote their offering as a one-stop-shop solution, covering all the stages of getting a product from the concept stage to scale-up manufacturing – and even beyond to ongoing product development and end-of-life processes.
These end-to-end capabilities are attractive to many companies in the life sciences sector as it reduces management complexity and can also reduce costs and risks.
Capacity
Getting access to available capacity is another major benefit of CDMOs and CMOs, whether that is compliance expertise to navigate the regulatory submission process, design and development expertise to develop a viable product, or manufacturing capacity to meet market demand.
Specific Expertise
As pharmaceutical and medical device products become more advanced with new and innovative technologies, it is becoming increasingly necessary to have access to specialist expertise. That expertise isn’t always available in-house, so partnering with a CDMO or CMO is an attractive solution.
Cost-Efficiency
Setting up in-house facilities and capabilities is costly, whether you are employing talent or investing in manufacturing equipment. These costs can be significantly reduced or eliminated by partnering with a CDMO or CMO.
This applies not only at the outset of a contract or project, but also ongoing as it will be the CDMO’s or CMO’s responsibility to ensure manufacturing equipment is upgraded and maintained, as well as to invest in new technologies.
Focus on Core Competencies
Partnering with a CDMO or CMO means your team can focus on your core business functions and competencies, such as R&D, marketing, and sales.
Scalability and Flexibility
Scaling up or down is easier when you partner with a CDMO or CMO. This flexibility ensures you can meet customer requirements when demand is high while minimising costs when demand is low.
Access to Advanced Technologies
Innovative and forward-thinking CDMOs and CMOs invest in the latest equipment and cutting-edge technologies to remain competitive. Partnering with a CDMO or CMO will mean you can also benefit from these investments.
Robust Systems and Infrastructure
CDMOs and CMOs will have robust and long-established procedures that can be immediately deployed on your project. This means you won’t have to spend time and resources developing these systems in-house.
Ultimate Responsibility for Patient Safety and Compliance
There is one final point to highlight before closing. More and more companies in the life sciences sector are partnering with CDMOs and CMOs as they calculate the benefits. However, it is always important to remember that, in the eyes of regulators (and patients), you remain ultimately responsible for product quality, patient safety, and regulatory compliance.
This needs to be considered when deciding to go down the CDMO/CMO route. If you decide this is the best option for your business, make sure you set clear expectations and requirements and ensure there is frequent, timely, and transparent communication. It is also important to continuously measure and monitor the performance of the CDMO/CMO, keeping a record of all monitoring activities in your quality management system.
By taking these steps, partnering with a CDMO or CMO can help companies in the life sciences sector achieve their objectives. As a result, we can expect the trend of growing CDMO/CMO use to continue.

Password Security Best Practices for the Life Sciences Sector
Pharmaceutical and medical device companies are high-value targets for cybercriminals, making cybersecurity a high-priority consideration. A key component of good cybersecurity is adopting password security best practices.
Good password security is important to protect IP and patient data, as well as ensuring operations can continue without the often significant interruptions that can occur as a result of a cyberattack. There are also compliance considerations in the life sciences sector, including the data integrity requirements of 21 CFR Part 11.
Even minor issues in relation to password security can result in a major breach, but before getting into the best practices for password security, it is important to highlight the wider cybersecurity context.
The Starting Point for Good Password Security
To properly protect your organisation’s infrastructure, data, IP, and operational integrity, it is critical to ensure there is a solid understanding at all levels of the importance of password security.
This understanding shouldn’t be limited to technical or procedural considerations, i.e., how many characters a password should have or how often passwords should be changed. Technical and procedural considerations are important, but it is also essential to understand the evolving threat landscape in relation to passwords.
This includes understanding the nature of social engineering and phishing threats, both of which can put even the strongest passwords at risk.
It is still essential to follow password security best practices, but passwords need to be considered in terms of your wider cybersecurity strategy, policies, and defences.
Password Best Practices
Use MFA
Multi-factor authentication (MFA) ensures a password alone won’t allow access to a system. MFA should be implemented as much as possible in pharmaceutical and medical device manufacturing organisations.
Put in Place Effective Password Security Tools, Procedures, and Policies
There are steps that can be taken at an IT and operational level to improve password security in pharmaceutical and medical device companies. This includes implementing MFA, as mentioned in the previous point.
Other steps that can be taken include:
- Implementing password monitoring technologies and/or password managers, the latter of which help users set and remember complex passwords. In fact, with a password manager, users don’t need to remember their passwords at all, as the system does it for them. The result is a good user experience with strong password security, but it is a solution that also comes with a crucial risk that should also be considered – the risk of the password manager itself becoming compromised.
- Ensuring systems, software, PLCs, devices, etc. are configured so users can’t use a password that has been used previously.
- Automatically disabling inactive accounts and locking down accounts after a preset number of failed login attempts.
There are also some password security tools and procedures that are best avoided. This includes knowledge-based authentication systems where users are asked to answer questions like their mother’s maiden name. These types of systems can weaken, rather than strengthen, password security.
Another commonly used practice that deserves careful consideration before being implemented is requiring employees to change their passwords after a predetermined period of time. There is growing consensus among cybersecurity experts that regularly changing passwords has little effect on improving security and can even weaken your defences.
For example, a user is more likely to write down their passwords if they have to remember new ones every two or three months. Alternatively, a user might alter just one character in their new password every time they are asked to change it. Hackers are aware of this practice of making minor modifications to existing passwords. If hackers are aware of it, they can beat it.
Encourage Good Password Structure
Best practices for password structure include:
- Password length is arguably more important than random complexity, so insisting on long passwords will help to improve password security.
- While password length is important, it is also beneficial to make passwords a random collection of numbers, uppercase letters, lowercase letters, and symbols.
- Educate users on the importance of not using the same passwords at work as they do on their personal accounts.
- Educate users to avoid using common words. In fact, using words should be avoided altogether. Phrases are better (because they are longer) but completely random collections of characters are best.
- Encourage staff to avoid common practices that meet password length and character requirements, but which do little to improve password security. While a password like Ph@rm@c3ut1caL might look hard to guess, using character substitutes like this is so common that hackers are very good at guessing these types of passwords.
Encourage Good Password Protection
Creating a unique and long password made up of a random collection of characters is only part of ensuring password security. It is also important that users protect the passwords they create. Best practices for protecting passwords include:
- Encourage staff to avoid writing down passwords, even if they think the location of the written password is secure.
- Prohibit the sharing of passwords.
- Prohibit the practice of a user logging into a system for someone else to use.
- Encourage employees to use a unique password for every account and system.
Move to a Single Sign-On Solution
Single sign-on solutions allow users to access multiple applications and systems by authenticating once. This provides a good user experience, but it can also improve password security. The benefits of single sign-on solutions include:
- Reduces password fatigue as users only have to remember one strong password, reducing the practice of choosing easier-to-remember passwords.
- Decreases phishing opportunities as users only have one set of credentials to remember. This makes them more aware of unusual requests that could be phishing attempts.
- Centralises system, device, and platform authentication to make it easier to monitor and manage user access.
- Reduces the attack surface as there are fewer passwords to steal and fewer routes of attack.
Continuous Vigilance
Finally, continuous vigilance is essential to maintain good password security in the life sciences sector. This includes continuously reviewing policies as well as new technologies that can improve security. It also includes providing staff with regular training on password security and other cybersecurity topics.
Nothing is completely foolproof when it comes to cybersecurity, but following these steps and best practices will help to significantly reduce risks.

Automated Guided Vehicles and Autonomous Mobile Robots in the Pharmaceutical Industry
Automated Guided Vehicles (AGVs) and Autonomous Mobile Robots (AMRs) are technologies that are transforming the pharmaceutical and medical device industries. When implemented properly, they can help manufacturers in the life sciences sector overcome some of the most difficult of today’s challenges, as well as improving productivity, efficiency, and quality.
Both technologies are similar as they are both material handling solutions that don’t require human intervention or involvement. In this blog, we’ll look at the differences between AGVs and AMRs, as well as suitable applications for these technologies in the life sciences sector and the benefits for pharmaceutical and medical device manufacturers.
What are AGVs?
AGVs are the older of the two types of material-handling robots as they date back about 70 years. Recent advances in technologies have now made AGVs a viable solution for many pharmaceutical and medical device production applications.
In brief, AGVs combine software and hardware systems to navigate and perform in predefined areas via fixed routes.
What are AMRs?
AMRs are also material-handling robots but, unlike AGVs, they don’t have to follow predefined routes. Instead, AMRs navigate autonomously using onboard sensors, cameras, and software. In other words, they can dynamically plan their route and avoid obstacles in real time.
Applications for AGVs and AMRs in the Pharmaceutical and Medical Device Industries
AMRs are a more recent technology, but there are applications for both AMRs and AGVs in the pharmaceutical and medical device industries. Those applications include:
- Transferring raw materials from storage and facility intake areas to the manufacturing line.
- Transferring product batches between manufacturing process stages.
- Transferring manufactured products for storage or shipping, or to assembly or packing stations.
- Transferring packaging materials to packing stations on the production line.
- Transferring waste material to disposal, recycling, and reprocessing areas.
- Storing and retrieving products in warehouses.
- Conducting various operations in clean room environments to reduce the need for human involvement and, as a result, lower the risk of contamination.
- Hazardous material handling.
The Benefits of AGVs and AMRs
Operators currently perform the tasks that AGVs and AMRs can automate in pharmaceutical and medical device manufacturing facilities. Automating these tasks brings a range of benefits:
- Efficiency improvements through enhanced productivity and greater workflow consistency. For example, AGVs can eliminate delays in getting raw materials to the production line.
- Various labour benefits, including being able to assign operators to more value-added tasks and reducing the labour that is required.
- Consistent performance as AGVs and AMRs don’t get tired, distracted, or sick. Instead, they perform tasks repetitively and consistently. Even low batteries don’t have to impact performance as systems can be set up in fleets, where an AGV or AMR with a low battery can return to a charging station while another, fully charged unit, takes its place.
- Speeds up production in a variety of ways, depending on how the AGVs or AMRs are deployed. For example, AGVs/AMRs can ensure raw materials are transferred to the production line efficiently and without delay.
- Optimises material flow throughout the manufacturing facility.
- Reduces human error in areas like inventory management and material transportation.
- Enhances traceability and overall process improvement, particularly if AGVs or AMRs are integrated with MES, ERP, and other business process, production, warehouse, and supply chain management systems.
- Enhances compliance with sensors logging data about the materials being transported.
- Enhances production oversight by using the data logged by the sensors on AGVs and AMRs.
- Improves worker ergonomics and safety as AGVs and AMRs reduce the need for manual handling in pharmaceutical and medical device production facilities.
- Improves hygiene and contamination control, especially in cleanroom environments where AGVs can reduce the need for human operators.
Humans and Machines Working Together
The future of pharmaceutical and medical device manufacturing facilities is one where humans and machines work together, with machines handling repetitive and monotonous tasks to leave engineers, technicians, and operators free for more demanding, challenging, and value-adding tasks. AGVs and AMRs are essential components of the factory of the future. Their importance will only increase as technologies develop and they become more integrated into the production environment.
« Previous 1 2 3 4 … 18 Next »




